LIMITATION OF USER RIGHTS WITH IAM PERMISSION BOUNDARY
Overview
After we have understood how IAM User, Group, Policy and Role work in the previous 2 labs. In this lab, we will continue to learn about IAM Permission Boundary.
What is IAM Permission Boundary?
IAM Permission Boundary is an advanced feature that allows us to limit the maximum permissions for a User or Group. Assuming we apply a Permission Boundary that only allows user EC2admin to administer the EC2 service, then he will not be able to have permissions on any other service even if he is assigned a higher permission Policy.
Therefore, the effective permissions of EC2admin users will include those allowed by both Permission Boundary and user EC2admin (Identity-based policy) permissions policy.
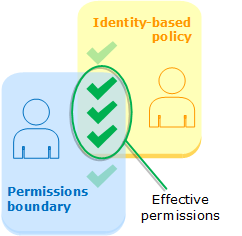
Why use IAM Permission Boundary?
Usually, when you are giving permission to IAM users, you think that just by building the user permissions policy carefully, you will be able to skip the step of using Permission Boundary.
However, as the number of users increases and the continuous changes in the work roles of the users require you to create more and more new permission policies, the management of permissions becomes complicated, thereby creating new permissions. vulnerability for privilege escalation (privilege escalation) in users.
To simplify permission management, instead of having to edit permission policies individually, you can apply Permission Boundary quickly and in bulk to help you close privilege escalation vulnerabilities.